Is there a way to configure a password for a stored session in PuTTY?
I know there is the capability to specify an "auto-login username" (under Connection/Data), but is there a way to do the same with the password?
Is there a way to configure a password for a stored session in PuTTY?
I know there is the capability to specify an "auto-login username" (under Connection/Data), but is there a way to do the same with the password?
For some versions of PuTTY, it's as simple as one of:
putty.exe mylogin@somewhere.com -pw mypassword
putty.exe somewhere.com -l mylogin -pw mypassword
If you want to connect using SSH, use this:
putty.exe -ssh root@somewhere.com -pw mypasswordforsomewherecom
For those using Windows, you can simply create a shortcut and pass in these parameters.
For example:
PuTTY - server.com"C:\Program Files\PuTTY\putty.exe" user@server.com -pw passwordIf your PuTTY does not support the pw parameter, you will need a public key as explained in:
Creating and Copying Your Key-Pair in PuTTY SSH Client (alternate up-to-date instruction source).
I simply save the password in the saved session name, then copy it into the clipboard and paste into the shell when prompted for a password. Saves time, lowers stress and is no more insecure than keeping the password in a file. Just in case you wonder: it will be saved in the Windows registry.
– NightKnight on Cloudinsidr.com Nov 22 '16 at 23:54-l mylogin works for me on Ubuntu with Putty 0.67
– iiic
Jul 24 '17 at 08:56
myname.bat Step 2. Edit myname.bat as example start E:\PuTTY\putty.exe root@ip_my_server -pw password -i "E:\SSH\private.ppk" -loghost "My title (remote ip)" Step 3. Doubleclick myname.bat
– Юрий Светлов
Oct 20 '20 at 14:02
Strongly advise using the public key mechanisms rather than sending passwords from the shell.
Here is one more reference for the setup.
Link to get latest PuTTY binaries (and check the FAQ).
I use WinSCP to “auto login” in PuTTY with a password. It's free, contains plenty of features, was created in 2000 and is still activity maintained. (WinSCP Wikipedia page)
STEP 1:
Options -> Preferences (View -> Preferences in Explorer interface). Then follow the screenshot below:STEP 2:
NOTE: Opening PuTTY from WinSCP can be done from either the login window, or from the SFTP window, which I find extremely handy:
I do tons of scripting at work and my flow is the following: WinSCP to open and save modifications remotely. VS Code to, hum... well code and Putty to run the script on the dev servers. I know I could do everything from VS Code, but this requires minimal configuration and everything runs as it will once in prod.
When I have to handle temporary servers with local creds, this is going to make my life a bit simpler.
– Prevok Feb 13 '24 at 14:41If you want to preserve saved options (such as pre-configured window sizes and tunnel proxy) and load a saved session to auto-login, use this approach: http://www.shanghaiwebhosting.com/web-hosting/putty-ssh-auto-login
putty.exe -load my_server -l your_user_name -pw your_password
Where 'my_server' is a saved session name.
PuTTY Connection Manager is a separate program that works with PuTTY. It can autologin and has an encrypted database holding the passwords.
I still prefer SSH keys though.
(Another downside is that it may no longer be supported by its original developer(s), and may only be available to download from third-party sources.)
There's a port of PuTTY called KiTTY which allows saving username / password.
The kitty_portable.exe is very handy; no installation is needed.
Combining two different packages for a security solution can be dangerous. This is the PuTTY-only way to do it, only using software from the PuTTY site.
You should first use PuTTYgen to create a key pair, then install the private key in PuTTY, and copy the public key to the remote site. Here is how you do this.
Download PuTTYgen, and execute it to generate a SSH2-RSA key. I'd use at least 4098 bits. Click the Generate button, move the mouse around, until the key pair is generated.
Once it's generated, your screen will look like this:

Describe the account in the "Key Comment" field. Then save the private key in one file, and the public key in another file.
Your public key will look like this:
---- BEGIN SSH2 PUBLIC KEY ----
Comment: "rsa-key-20160822"
AAAAB3NzaC1yc2EAAAABJQAAAgEA5Kp+G9z8eE0MpPZL9JZksstIa3L9JEND6ud1
1IiD6f1jw/7Lv7CvZcCdk/OVMT+DlTbryRoqfbNMLkjajqNTUGBAscTduUtPYuQt
YEQgtbJd/hyHtTHK9X/wiKeQr7LjHZcEg3osYh+MzZFscldQM/a/Z26AKh81EC9X
uIu98snjOBM0ysb14Uu7hMvti5Xd3kSW7ctL2j1ORuRgZX6LHihaezvsBFI5S/lZ
4v/yxymRKQnyV6OkMNMXESJpXh3cTMIIGtDJtbbYvh5Qs0f3O1fMiQYyz2MjGphd
zBihq85a1SHx0LBk31342HsCiM4el//Zkicmjmy0qYGShmzh1kfZBKiBs+xN4tBE
yjRNYhuMGP2zgpr9P/FO1buYdLah5ab3rubB5VbbRP9qmaP2cesJS/N91luc099g
Z+CgeBVIiRr1EYTE8TqsSBdvmu3zCuQgDVcSAoubfxjM4sm3Lb6i4k4DJmF57J6T
rcyrSIP9H/PDuBuYoOfSBKies6bJTHi9zW2/upHqNlqa2+PNY64hbq2uSQoKZl1S
xwSCvpbsYj5bGPQUGs+6AHkm9DALrXD8TX/ivQ+IsWEV3wnXeA4I1xfnodfXdhwn
ybcAlqNrE/wKb3/wGWdf3d8cu+mJrJiP1JitBbd4dzYM0bS42UVfexWwQSegDHaw
Aby0MW0=
---- END SSH2 PUBLIC KEY ----
You have to edit this to a form that is suitable for your remote site. Let's assume it's a Linux machine using ssh.
Edit the file so it has three fields:
So it should look like this when done
ssh-rsa AAAAB3NzaC1yc2EAAAABJQAAAgEA5Kp+G9z8eE0MpPZL9JZksstIa3L9JEND6ud11IiD6f1jw/7Lv7CvZcCdkOVMT+DlTbryRoqfbNMLkjajqNTUGBAscTduUtPYuQtYEQgtbJdhyHtTHK9XwiKeQr7LjHZcEg3osYh+MzZFscldQMaZ26AKh81EC9XuIu98snjOBM0ysb14Uu7hMvti5Xd3kSW7ctL2j1ORuRgZX6LHihaezvsBFI5SlZ4vyxymRKQnyV6OkMNMXESJpXh3cTMIIGtDJtbbYvh5Qs0f3O1fMiQYyz2MjGphdzBihq85a1SHx0LBk31342HsCiM4elZkicmjmy0qYGShmzh1kfZBKiBs+xN4tBEyjRNYhuMGP2zgpr9PFO1buYdLah5ab3rubB5VbbRP9qmaP2cesJSN91luc099gZ+CgeBVIiRr1EYTE8TqsSBdvmu3zCuQgDVcSAoubfxjM4sm3Lb6i4k4DJmF57J6TrcyrSIP9HPDuBuYoOfSBKies6bJTHi9zW2upHqNlqa2+PNY64hbq2uSQoKZl1SxwSCvpbsYj5bGPQUGs+6AHkm9DALrXD8TXivQ+IsWEV3wnXeA4I1xfnodfXdhwnybcAlqNrEwKb3wGWdf3d8cu+mJrJiP1JitBbd4dzYM0bS42UVfexWwQSegDHawAby0MW0= rsa-key-20160822
Personally, I would copy the file over to the Linux machine, and then edit it, because editors like vim are much more tolerant of long lines. I'd use the 'J' command to join two lines, then search for spaces and delete the spaces between the lines. When I copied this file over to Windows, the system insisted on splitting the single long line into multiple lines with "\" between the lines. Yuck. To continue...
Log into the remote machine, and copy/edit, then append the public key into the ~/.ssh/authorized_keys file in the same format as the other keys. It should be a single line. There should be three fields on a single line. The first says "ssh-rsa". The second is the key which should end with the characters "=" the third field is optional, and will contain what you put in the Key Comment field.
If this is the first time you have created the ~/.ssh/authorized_keys file, make sure the directory and file are not group or world readable.
Once this is done, then you have to create a PuTTY session where the private key is used.
In the PuTTY session, go to Connection=>SSH=>Auth and click browse and select where you stored your private key "It's a *.ppk" file.
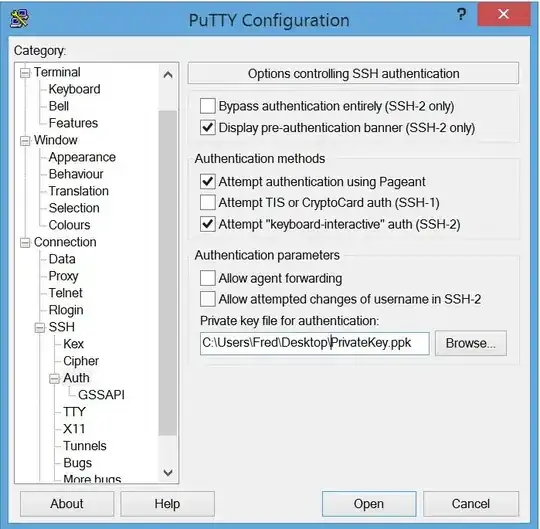
Then save this session (I'm assuming you also set up the account, IP address, etc.).
Once this is done, you just have to select the session, and you are logged in.
A more secure way is to store your private key in an encrypted file, using a passphrase. Then use Pageant to manage your passphrase. That way the private key is always encrypted, and you only have to type in a passphrase once in a while.
I use mRemote on Windows; it can store usernames and passwords for SSH, RDP, VNC and Citrix.
Yes, there is a way. Recently I added a password saving feature for PuTTY 1.5.4 for both Linux and Windows. You can download binaries and source from Oohtj: PuTTY 0.62 with a password saving feature.
Tunnelier - saved passwords encrypted locally. It also has a sFTP GUI as well as SSH windows.

If the connection is authenticated by a public key and password, consider using Pageant which is part of the PuTTY suite.
You can add your private keys to Pageant with the associated password. Assuming you've got the correct username configured in PuTTY, you will be authenticated transparently.
It doesn't store your keys/passwords long-term so you'll have to re-add next time you launch it. There is a command line option to launch and add keys in one go.
"C:\Program Files\PuTTY\Pageant.exe" key1.ppk key2.ppk key3.ppk
It will prompt for a password if required.
And best of all, it's part of the PuTTY suite, so you've probably already got it on your machine.
If you use the following way, don't forget to add "" to enclose your session name, or it may fail to load the session. For example,
putty.exe -load "my session name",
The general form is:
putty.exe -load my_server -l your_user_name -pw your_password
I prefer doing like this on a Windows machine. Save the PuTTY executable in a folder, say "mytools", and run this command from command prompt:
tools>mytools 10
10 is the last octet of your IP address. That's it.
@ECHO OFF
set PUTTY=E:\tools\putty.exe
start %PUTTY% root@192.168.1. %1 -pw yourpassword
reg files http://www.igvita.com/2008/04/14/custom-putty-color-themes/ as my color scheme but can i use it somehow ?
– Em Ae
Feb 21 '13 at 17:57
-load cli option in your putty shortcut, e.g.: start %PUTTY% -load "myCustomColorSession" -l yourusername -pw yourpassword
– Amit Naidu
May 20 '20 at 03:22
I would like to explain more on Emrald214s answer on MTPutty as its a nice free software.
MTPutty - Multi-tabbed putty (portable version because of corporate installation limitations for many users) as it helps to connect to many servers and its easy to organize in folders with this free software.


in above script SLEEP is for wait in between commands in miliseconds. Alternatively for default wait time you can specify "wait period before typing commands" in script window instead of _SLEEP command
Note:
This software helps a lot in daily operation if you need to deal with many servers.
Install MTPuTTY and your problem should be solved. You can even execute a bunch of scripts after logging into Putty.
If the command history is a security concern, go the public key route (as your plaintext password specified in the -pw option is stored in the command history).
If you work under windows you can create a .bat file with a text editor then put
putty.exe -ssh user@Ip_Address -pw password
mRemoteNG allow you to save username and password in its connection, or username in putty connections. I prefer it because it's multitab and open source.