This PE file destroys its import address table. However, all the function addresses are in this _rdata segment here:
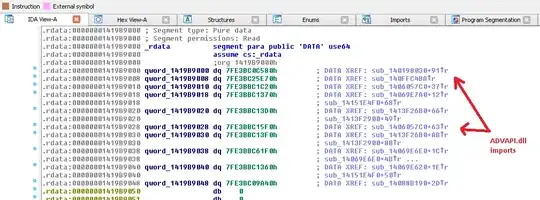
Any straight forward way to rename these functions?
This PE file destroys its import address table. However, all the function addresses are in this _rdata segment here:

Any straight forward way to rename these functions?
Before you dump the process's memory to disk, use a tool like Scylla to reconstruct the Import Table.
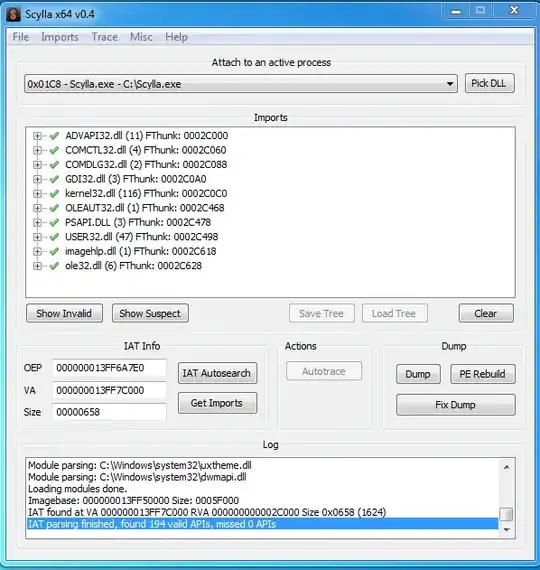
While in debugger, select the import table and run idc\renimp.idc.
Top comment from the file:
/*
Rename imports.
This script renames entries of a dynamically built import table.
For example, from a table like this:
dd offset ntdll_NtPowerInformation
dd offset ntdll_NtInitiatePowerAction
dd offset ntdll_NtSetThreadExecutionState
dd offset ntdll_NtRequestWakeupLatency
dd offset ntdll_NtGetDevicePowerState
dd offset ntdll_NtIsSystemResumeAutomatic
dd offset ntdll_NtRequestDeviceWakeup
dd offset ntdll_NtCancelDeviceWakeupRequest
dd offset ntdll_RtlQueryRegistryValues
it will create a table like this:
NtPowerInformation dd offset ntdll_NtPowerInformation
NtInitiatePowerAction dd offset ntdll_NtInitiatePowerAction
NtSetThreadExecutionState dd offset ntdll_NtSetThreadExecutionState
NtRequestWakeupLatency dd offset ntdll_NtRequestWakeupLatency
NtGetDevicePowerState dd offset ntdll_NtGetDevicePowerState
NtIsSystemResumeAutomatic dd offset ntdll_NtIsSystemResumeAutomatic
NtRequestDeviceWakeup dd offset ntdll_NtRequestDeviceWakeup
NtCancelDeviceWakeupRequest dd offset ntdll_NtCancelDeviceWakeupRequest
RtlQueryRegistryValues dd offset ntdll_RtlQueryRegistryValues
Usage: select the import table and run the script.
Known problems: if the dll name contains an underscore, the function
names might be incorrect. Special care is taken for the ws2_32.dll but
other dlls will have wrong function names.
*/
You're most likely using a process dump. those addresses would depend on the Windows version and service pack. If you had a chance to run it in a VM, try volatility. do a procdump then impscan. impscan can give you an idc that renames those addresses to their respective API names.
this method works well even with non-PE injected codes.
https://github.com/volatilityfoundation/volatility/wiki/Command%20Reference%20Mal#impscan