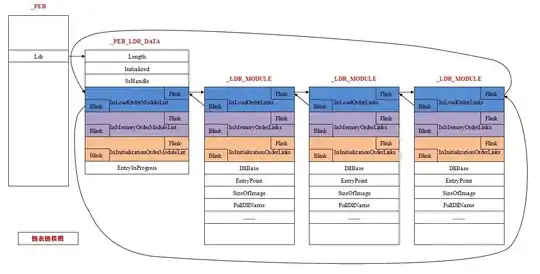
I am trying to get the base address of ntdll.dll over the PEB. So, what I did was to dump the PEB (d fs:[30]). Then, I tried to get to PEB_LDR_DATA over the offset 0xC. Over the offset 0x1C of PEB_LDR_DATA I found the the pointer of InInitializationOrderModuleList and I was told that I can find the ntdll.dll address there. And that I should first find the address of kernel32.dll (which is always the second entry). So, I was able to find the address of kernel32.dll but it seems like I can't find the address of ntdll.dll.
00251ED8 .ܛὈ%Ậ%ὐ%Ẵ%.....@ᐴ@怀.TVٜڔ倀...뉨粘뉨粘趨即....ꮫꮫꮫꮫ......ܨ‐%Ỡ%‘%Ứ%
00251F58 †%Ẽ%.粑Ⱘ粒怀:Ȉ퀨粘⅘粓䀄耈..니粘니粘뾿䠂....ꮫꮫꮫꮫ......ܵC:\WINDOWS\system32\
00251FD8 kernel32.dll.ꮫꮫꮫꮫﻮﻮﻮ......߁⅐%Ὀ%⅘%ὐ%Ⅰ%%.粀똾粀耀@Bᾰ%Ῐ%䀄耈..늰粘늰粘뿀䠂
00252058 ....ꮫꮫꮫꮫ.....ߎC:\WINDOWS\WinSxS\x86_Microsoft.VC90.CRT_1fc8b3b
002520D8 9a1e18e3b_9.0.21022.8_x-ww_d08d0375\MSVCR90.dll.ꮫꮫꮫꮫ.....ߩẬ%‐%
00252158 Ẵ%‘%Ẽ%†%.硒ⵀ硔 .¾À⁸%℠%䀆逈..닀粘닀粘㷎䜱....ꮫꮫꮫꮫ....ߊ.ᓮîŸ%Ÿ%ﻮﻮﻮﻮﻮﻮﻮﻮﻮﻮﻮﻮ
This is the part where I have found the kernel32.dll. But in the fact of that this a linked list. Shouldn't I be able to find ntdll.dll too?
When, I open up the window of "Executable Modules" I can see the ntdll.dll but it seem I am not able to find the base address inside of the Struct.
Please tell me if you need clarification or if I am grievously mistaken.