I'm running a 64-bit MS Windows 7 with all updates installed. About 1 or 2 weeks ago I've noticed that whenever I restart the OS, the virtual memory pages (of whatever process), corresponding to system libraries like ntdll.dll and kernel32.dll are slightly different.
I'm not talking about the base address of the loaded modules, because I know that changes due to ASLR. I'm talking about the actual contents of the loaded modules, which as far as I know was not affected by ASLR implementations on Windows.
To illustrate what I mean, let me show you the following screenshot that compares 2 binary instances of ntdll.dll captured before (top-half) and after (bottom-halt) one OS restart:
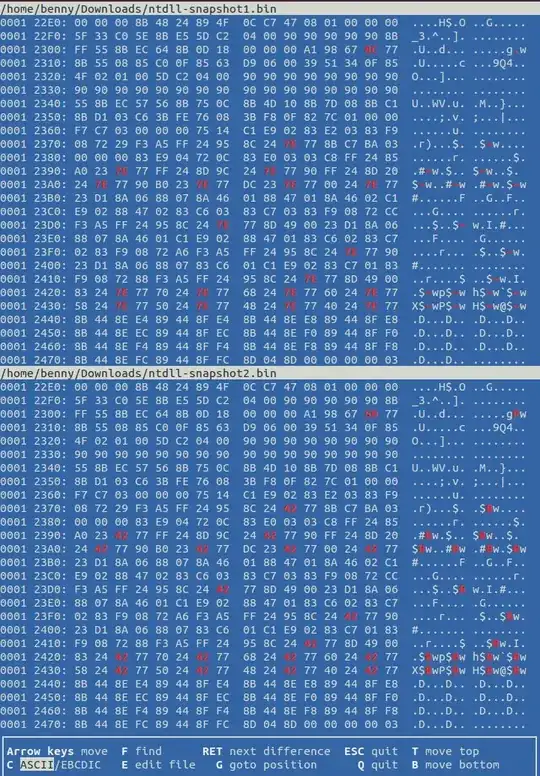
The picture shows just a small part of ntdll.dll and therefore just a few differences. However, there are more. The size of these DLLs don't change, only some bytes at particular locations.
I obtained the 2 binary instances which are compared in the previous picture using Process Hacker like so:
- Right-click a process and select Properties
- Go to the Memory tab and scroll-down until you find several entries having the name: ntdll.dll: Image (Commit)
- Double-click one of these entries (I chose the one that had 856kB)
- Press the Save... button to store the contents to a binary file on the HDD.
Question 1: What is causing these bytes to change?
- Sub-question 1.1: Is is some sort of protection mechanism?
- Sub-question 1.2: Was it recently introduced?
- Sub-question 1.3: Can it be disabled?
Question 2: What do these changing bytes represent in the code of the DLLs?
dumpbin /relocations ntdll.dlland compare the listed addresses against the changes. – Igor Skochinsky Mar 18 '14 at 13:53dumpbinas you indicated and compared the listed addresses against the changes. As a matter of fact it seems that no relocations were applied onntdll.dll. And the changes that are visible in my picture are due to the system DLLs being linked with/DYNAMICBASE– Benny Mar 20 '14 at 12:59