I'm trying to learn Buffer Overflow Here is the vulnerable code
#include <stdio.h>
#include <string.h>
int main(int argc, char const *argv[])
{
char buffer[64];
if(argc < 2){
printf("The number of argument is incorrect\n");
return 1;
}
strcpy(buffer, argv[0]);
return 0;
}
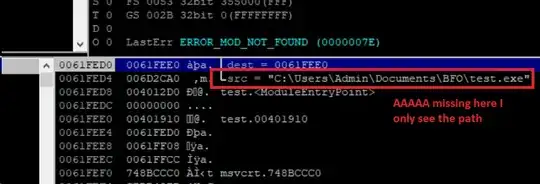
The problem is that when I try to run the code in Immunity Debugger, I don't see AAAAAAA in the source in the stack pane I see the path to my test.exe. Later, I don't see 0x41s ....obviously
What is happening ?