Hello,
I am having an exe file that I am trying to deobfuscate and debug using dnspy. The exe file was written in C# and obfuscated with unknown deobfuscate according to de4dot! I tried to all my known methods to procced but still I was not able to fully deobfusticated it.
Analysing the File
- Exeinfo PE
I tried to analysie the file with exeinfope to check which obfustactor was used but I only got [obfus/crypted].
Microsoft Visual C# / Basic.NET / MS Visual Basic 2005 [ Obfus/Crypted- StrongName set ] - EP Token : 06000080 , Overlay : 403900... Nothing discovered
- Dnspy
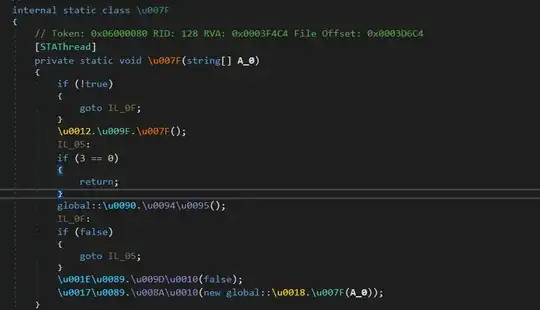
Opening the file in dnspy but the code wasn't readable, especially the methods and the functions name are in unicode form.
My Attempts:
- Tried to deobfustace the file with de4dot, but I get "Detected Unknown Obfuscator" followed by an error.
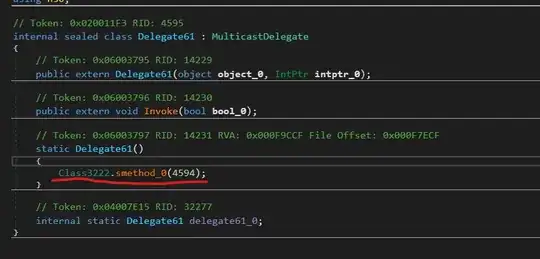
- Tried a modded version of de4dot, and I was able to deobfustacte the exe,but all functions shown as "delegate". The exe file was detected as "Unkown Obfustactor" as well, but managed to cleaned it.
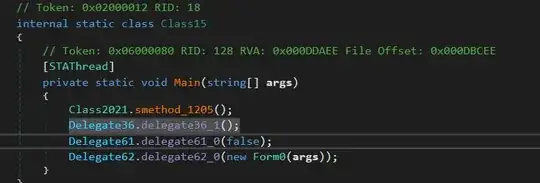
- Tried to debug the cleaned verison but when I start dnspy I get an exception (System.NullReferenceException)

My Questions:
- Which obfustactor was used ?
- Why all functions are defined as "delgate"?
- Why did I get the null exception while debugging
Thanks...
UPDATE 20/08/2020
While looking through the code, I found that all "delegate" calls are referred to a function which takes an intger but I couldn't find any obvious return from this function, what I do think it returns the function and method name but... HOW!!