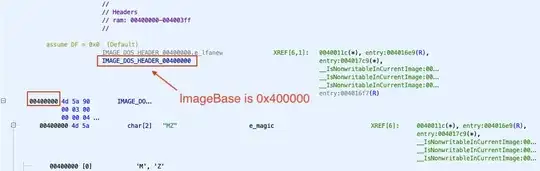
I'm reversing a malicious 32-bit x86 Windows executable. Statically reviewing PE headers in Ghidra, I see that ImageBase is set to 0x400000 as expected. However, when the binary is loaded into memory, the initial RVA does not match the ImageBase defined in the file. For example, I have seen the in-memory base address set to 0x4B0000 and 0x900000. This behavior occurs on a clean VM, and when debugging with Immunity and x32dbg as well as IDA Free.
My understanding is that the Windows loader reads ImageBase and uses that offset to begin mapping sections into virtual address space. Because system code handles loading, and my system is clean upon first execution, my assumption is that the unusual ImageBase is a symptom of a loader nuance rather than tampering. I've never encountered this scenario and would appreciate any insights.
MD5: 1f63d04ee95ea041f2f6b1e818d94a7c
SHA1: 823ad6abb05f2393c44cf4b7f1d00e32ac04d1d1
ImageBase set to 0x400000 when viewing PE headers in Ghidra:
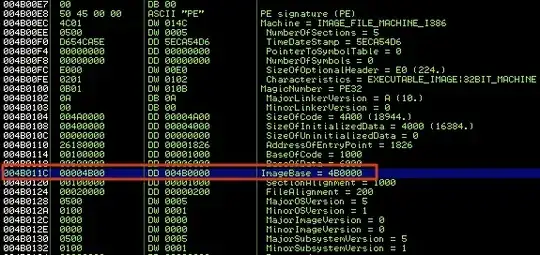
ImageBase in memory-mapped PE header (0x4B0000) does not match ImageBase set in static file:
PE sections mapped into memory with ImageBase at 0x4B0000

0x400000ImageBasewhen loading the binary into various debuggers. I note this here only to rule out ASLR as the cause of the RVA randomization in this particular case. – j5bb Aug 19 '20 at 13:19Also, in each disassembler: Ghidra, IDA, Binary Ninja etc, there is a setting to rebase the database to match the base address in memory. This can alleviate some of the pain.
– Utkonos Apr 24 '22 at 05:23