I'm curious about this __security_cookie that I keep seeing all over the msvcp140.dll from my Windows 10 x64 (insider build.)
Here's an example:
Note that the address for indirect function call (or qword_18009FBD0) is taken somewhere from the .data section:
Then it is XOR'ed with the __security_cookie:
I thought that __security_cookie is something that is used on the stack to guard against buffer-overflows. So they must be using some new security technique. Any idea what that is?
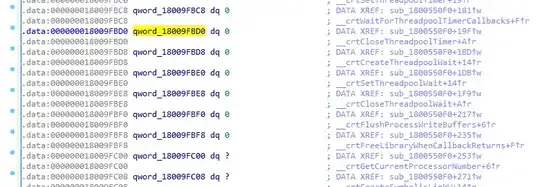
And a follow up question. I'm trying to statically analyze this binary code with IDA and this __security_cookie makes it very difficult to see what function is actually being called. For instance, here's how qword_18009FBD0 looks like:
Any idea how to make those function addresses more legible?