The document you linked to is not a patent, it is a patent application. Since claims are usually changed and narrowed during the prosecution of a patent application it is hard to know whether you will infringe on the subsequent patent is or when it is issued. You can't enforce applications, only patents. However, I did find a US patent associated with this application family: US9529896B2.
In order to infringe on a patent, you must implement each and every step of at least one claim. Here is the first claim of US9529896B2.
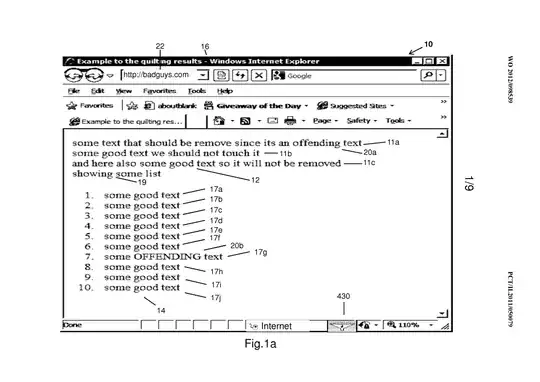
A method for on-line filtering of undesired content from a presentation built from a source code and for displaying the filtered
presentation to a user comprising:
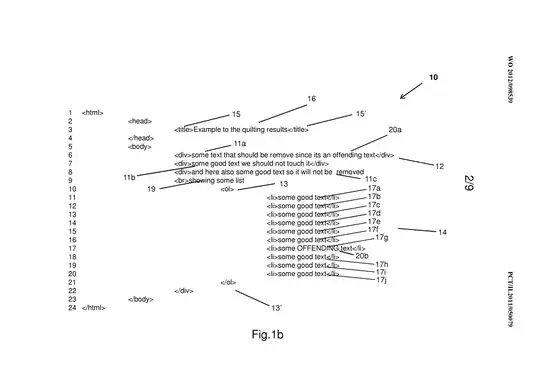
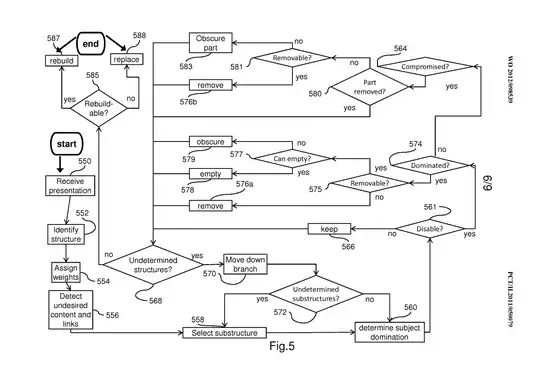
a) identifying a plurality of
structures and a plurality of substructures of at least one structure
of said plurality of structures in the source code; said at least one
structure having a beginning marked by a first marker and an end
marked by a second marker; each substructure of said plurality of
substructure having a respective beginning marker and wherein each
said respective beginning marker is located between said first marker
and said second marker and wherein each of said plurality
substructures beginning with said respective beginning marker ends
with a respective end marker;
b) detecting the undesired content in
said plurality of substructures;
c) determining at least one
substructure dominated by said undesired content;
d) disabling said at
least one substructure according to said determining; said disabling
resulting in a a sanitized structure, without the undesired content;
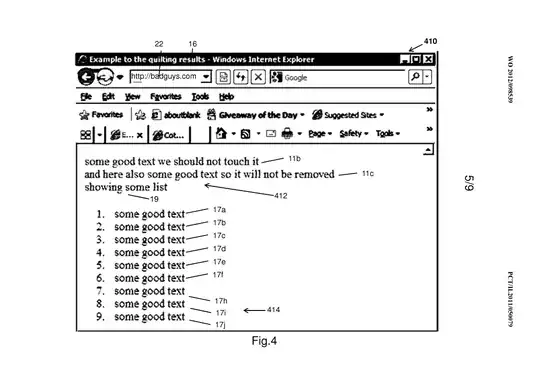
e) removing said sanitized structure from said presentation when said
sanitized structure does not correspond to said structure such that
displaying said sanitized structure in the presentation would make the
user aware of said disabling and arouse a curiosity of the user of
said presentation towards a said undesired content;
f) sending said
source code including an outcome of said disabling and said removing;
to an output device for rebuilding and display to the user;
g) performing a first action when a combination of a first word and a
second word is detected between said respective beginning marker and
said respective end marker of a single substructure of said plurality
of substructures: and
h) performing a second action different from
said first action and when first word is in said single substructure
and said second word is not in said single structure and said second
word is in another substructure of said plurality of substructures.
As you can see, this is a very long and detailed claim. Long claims are actually considered narrower than short ones since you only need to avoid a single step to keep from infringing on it. For instance if a claim has steps a, b, c and d and you only implement a, b and d, you should avoid infringement. However if you implement a, b, c, d and e (new stuff), you will infringe. The other independent claim is claim 7 which is also quite long. You know your process better than I do so compare what you are doing to these two claims and see if you are avoiding at least one step in each.
Since you received a warning letter, I think you absolutely need to consult with a patent attorney. The attorney can provide an assessment of freedom to operate of your implementation and how to respond to the patent holder.