Background
Microsoft certifies Windows 7/8 as well as Server 2008 R2 and 2012 to be FIPS-140-2 compliant. Actually they certify just a small crypto core, bcrypt.dll (the library, which is unrelated to bcrypt, the key derivation function). Microsoft's FIPS-140-2 architecture is detailed here. Also, their FIPS-140-2 AES certificate on NIST's listing is certificate #2216, in detail here. You can see in the listing that AES in GCM mode was tested with comments IV Lengths Tested: ( 8 , 1024 ) , 96BitIV_Supported , GMAC_Supported. I do see other vendors also having an additional flag/comment OtherIVLen_Supported in their FIPS AES certificate that MSFT's own FIPS certificate lacks.
Issue
We tested bcrypt.dll for AES in GCM mode with the test vectors found in the AES GCM paper (hosted on NIST). We found that Windows' bcrypt.dll throws an error (NT_STATUS = An invalid parameter was passed to a service or function.) when using IVs that are NOT 96 bits. So basically the test vectors 5, 11, 17 and 6, 12, 18 fail as those two groups use IVs of size 64 bits and 480 bits respectively. The results are
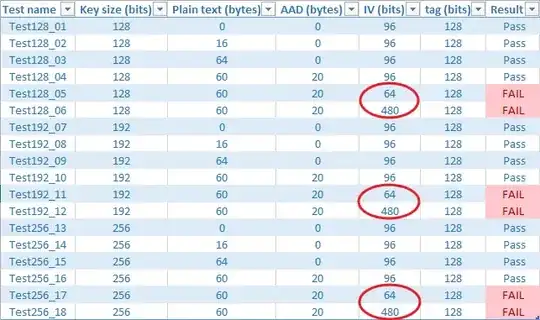
Question
I know that IV size != 96bits means additional processing but how can they clear certification despite failing IV sizes of 64 and 480 bits? Or is IV at 96 bits the only required IV length needed for passing?